Top Cybersecurity Tools 2024
With the rise in crime on the Internet, so does the need for protection. This is why cybersecurity is gaining momentum. Cybersecurity is the epitome of all measures to protect networks, applications, and devices. This solution is aimed at securing…
How to Conduct a Vulnerability Assessment on Your Company’s Digital Infrastructure
Vulnerability scanning is the act of scrutinizing a piece of digital infrastructure, software or hardware, to identify security issues. They are a crucial component of a vulnerability management approach, increasing your chances of protecting your system against leaks, viruses, and…
Post-Pandemic Cybersecurity Issues Plaguing Modern Digital Business
In the wake of post-COVID pandemonium, many business organizations lost their direction amidst the immense shift to the digital corporate environment and landscape. New times demand new measures, and many organizations have migrated to cloud, remote, or hybrid setups. While…
Top 7 Mobile Wallet Cybersecurity Attacks
Mobile wallets have become a popular and convenient way to pay for goods and services, but with convenience comes the risk of cyber-attacks. As mobile payments become increasingly prevalent, cybercriminals are finding new and creative ways to exploit vulnerabilities in…
A Quick Look at the Cybersecurity Standards and Frameworks
All organizations must take steps to prevent cybercrime and security breaches, but determining which cyber security measures to prioritize can be difficult. Also, with developing and sophisticated cyberattacks, only one security measure may not be as useful as you think.…
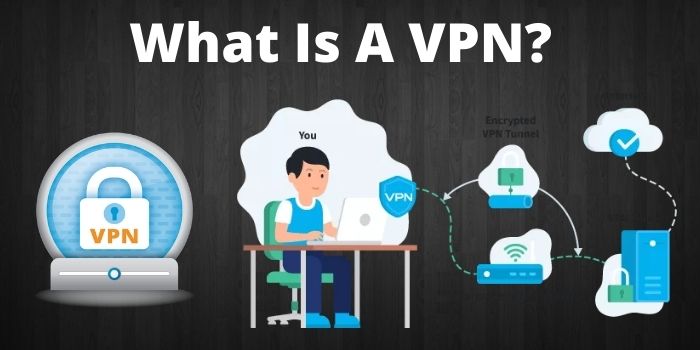
What is VPN?
When you want some privacy, a VPN is the foremost best way to safeguard yourself on the extensive, unsecured internet. Use of VPN when you travel to a foreign country can grant you access for services that are restricted in…
5 Cybersecurity Solutions Every Business Needs
As the number of threats to businesses and individuals increases, it is vital to have cybersecurity solutions in place. Here are five services that every business needs. 1. Endpoint Security Endpoint security provides a way to monitor and control all…
How Bulk IP Geolocation Helps Cybersecurity Pros
Despite the clampdown on obtaining personally identifiable information (PII) without user consent due notably to the implementation of strict privacy regulations, or maybe because of it, bulk IP geolocation data has become useful in tracking down cybercriminals. Bulk IP geolocation…
What is Doxxing & How You Can Ensure Internet Security?
The Internet has drastically affected the way we live and communicate. Sadly, bullying and offensive communication have also found their way online. Doxxing is just one of the examples of how information availability can work against you. What does Doxxing…
6 Effective Steps to Carry Out Penetration Testing Successfully
When it's about data security and cyber security, most companies (if not all) are on their toes to discover vulnerabilities and correct them ASAP. There’s no better way to proactively deal with hackers and ensure network security than carrying out…